Customizing the IAM Role
Using CloudFormation Template
ElasticDW needs permission to access your cloud environment. This is accomplished by creating an IAM Role. You have the option of using the boilerplate (recommended), or customizing the Cloud Formation template provided. Here is an small sample of our CloudFormation template. If you would like to customize this or use Terraform, send an email to info@full360.com to schedule a security review.
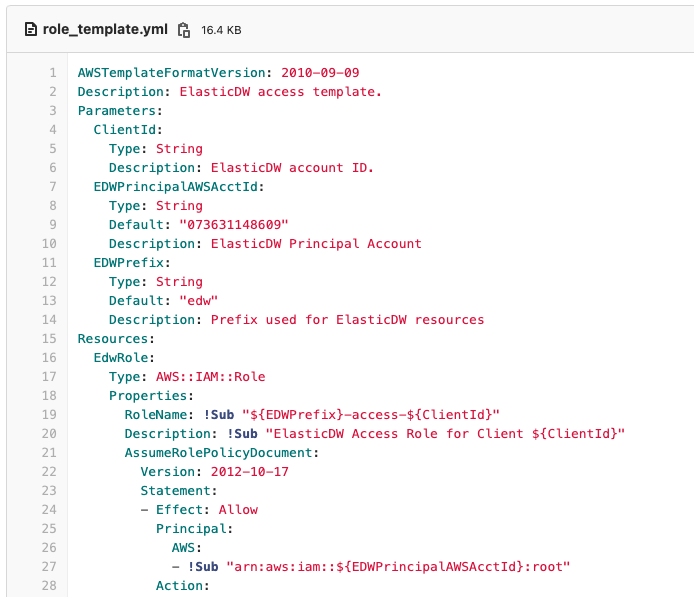
Once the Cloud Formation document has been created, upload it to your environment. It will be named similar to the format of f360-edw-master-role. It authorizes ElasticDW to create the role and policies necessary for operation.
Using CLI
-
Create the CloudFormation stack on your AWS account using the corresponding AWS CLI CloudFormation deploy command Example:
aws cli cloudformation deploy \
--stack-name edw-access-role-xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx \
--template-file "/path/to/the/downloaded/template.yml" \
--parameter-overrides ClientId=xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx \
--capabilities CAPABILITY_IAM CAPABILITY_NAMED_IAM
--template-file: Provide the full path of the downloaded template in this flag
--stack-name: Provide a stack name for this flag, e.g edw-access-role-xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
--parameter-overrides: Provide a ClientId parameter with your Client ID ( xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx ) as its value for this flag.
Using Terraform
Advanced users may also choose to setup these authorizations via Terraform. Prerequisites for the creation of ElasticDW roles can be found on Github
